什么是MOAC
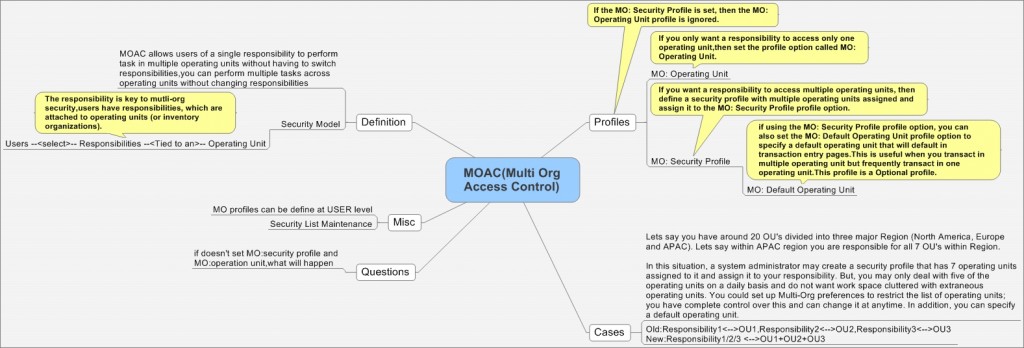
MOAC(Multi-Org Access Control)为多组织访问控制,是Oracle EBS R12的重要新功能,它可以实现在一个Responsibility下对多个Operation Unit(OU)进行操作。MOAC允许用户在不切换responsibility的情况下,在一个responsibility下处理多个OU组织的事务。
User --> Responsibilities --> Single Operation Unit Mode / Multiple Operation Unit Mode
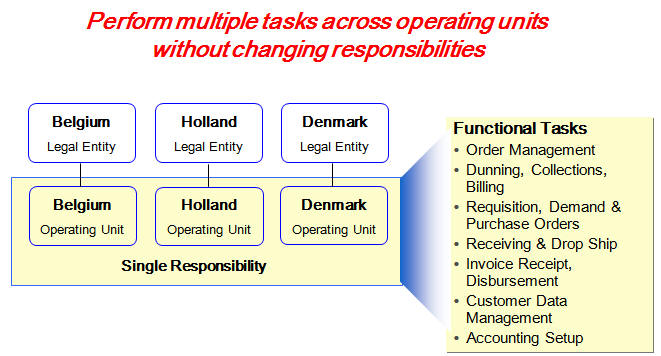
一个应用场景:
某集团公司下边主要分为三个区域(北美,欧洲,亚太),亚太区你是一采购部经理,负责所有七个Operation Unit。
这种情况下,系统管理员可以创建一个security profile,这个security
profile设置成可以访问这七个亚太组织,并把这个security
profile赋予到你的responsibility下,这样你就能在同一个职责下访问这七个OU了,就不用不停地切换职责来访问不同OU了。
另外如果你要经常处理中国OU下的事务,那么你可以设置Profile:MO: Default Operating Unit到中国,那么业务默认的OU就是中国了。
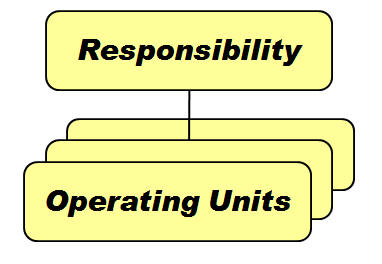
MOAC相关的Profile
有三个主要的Profile
MO: Security Profile :provides access to multiple operating units from a single responsibility.If the MO: Security Profile is set, then the MO: Operating Unit profile will be ignored.
MO: Default Operating Unit :If
you set the MO: Security Profile profile option, you can also set an
operating unit as the default operating unit using the MO: Default
Operating Unit profile option. This is useful when you transact in
multiple operating unit but frequently transact in one operating unit.
MO: Operating Unit :MO: Operating Unit profile option only provides access to one operating unit.
MOAC profiles rules
1)
If the profile option “MO: Security Profile” is not set, then “MO:
Operating Unit” value is used as the default Operating Unit even if “MO: Default Operating Unit” profile is set to a different value.
2)
If the profile option “MO: Security Profile” is set and gives access to
only one Operating Unit, the default Operating Unit will return this
value even if “MO: Default Operating Unit” is set to a different value.
3) If the profile option “MO: Security Profile” is set and gives access to multiple Operating Units :
- If the profile value “MO: Default Operating Unit” is set, it is
validated against the list of Operating Units in “MO: Security
Profile”.
+ If the Operating Unit is included in the security profile then it is returned as the default value.
+ Else there is no defaulted Operating Unit .
- If the Profile Option “MO: Default Operating Unit” is not set, then there is zero (no) default Operating Unit.
单组织的案例
单组织即一个Responsibility只访问一个OU,设置情况大体如下,对于职责:Manufacturing and Distribution Manager,
MO: Operating Unit=Vision Operations
MO: Security Profile=空
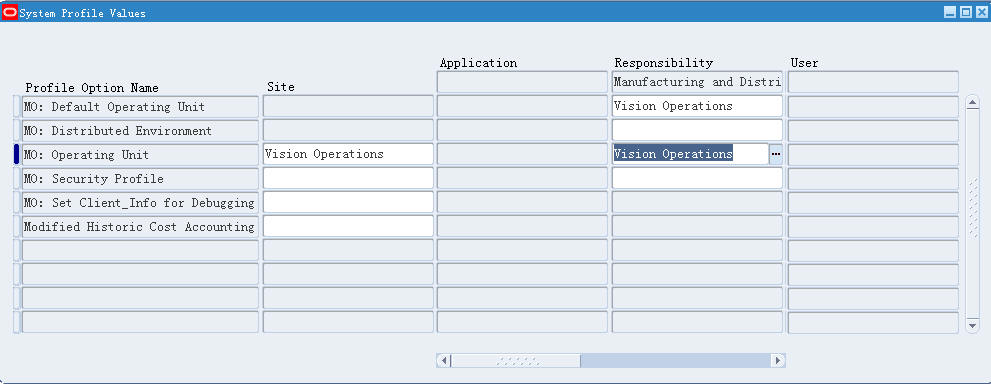
这样我们在使用职责:Manufacturing and Distribution Manager的时候,就只能访问到Vision
Operations的数据,比如创建的PO,这个PO只能处于OU:Vision Operations下,另外所选取的供货商也只能是Vision
Operations下的。
多组织的案例
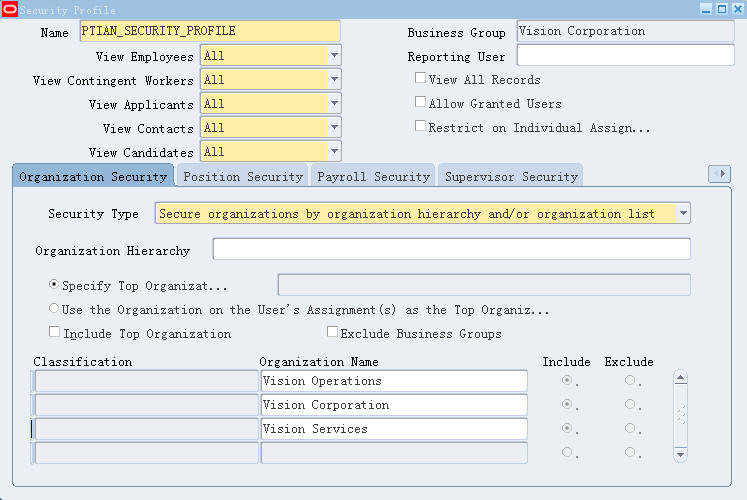
首先定义一个Security Profile,路径:HRMS Super User Responsibility > Security > Define Security Profile,Business Group:Vision Corporation,'Security
Type'选择'Secure organizations by organization hierarchy and/or
organization list',并且我们把在Organization Name列表中添加三个OU:Vision
Operations,Vision Corporation ,Vision Services.
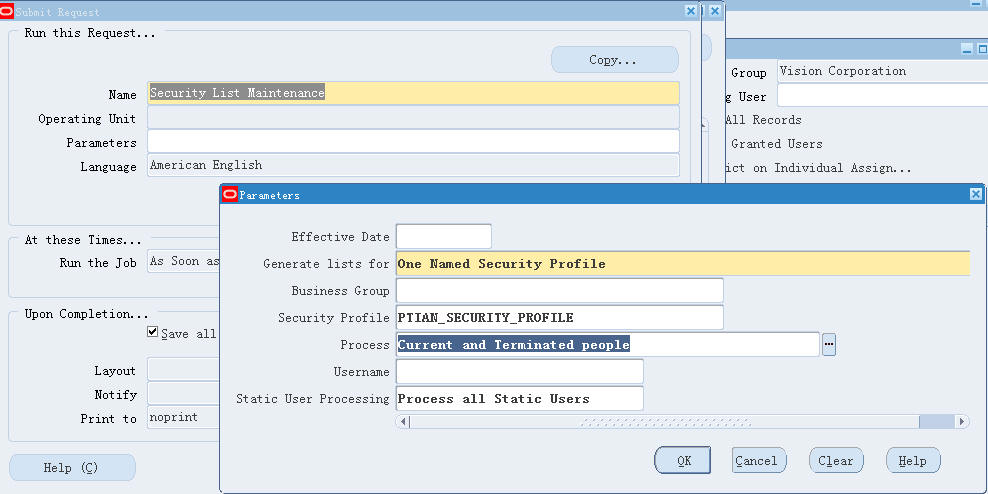
保存定义的Security Profile,然后在HR职责下,运行“Security List Maintenance” program,“Generate lists for”= One Named Security Profile ,Security Profile是刚刚定义的'PTIAN_SECURITY_PROFILE'。
Security List
Maintenance的作用是让你定义的Security Profile生效,能够设置到Profile "MO: Security
Profile"(The Security List Maintenance concurrent program must be run
each time you add or change Security Profiles.)
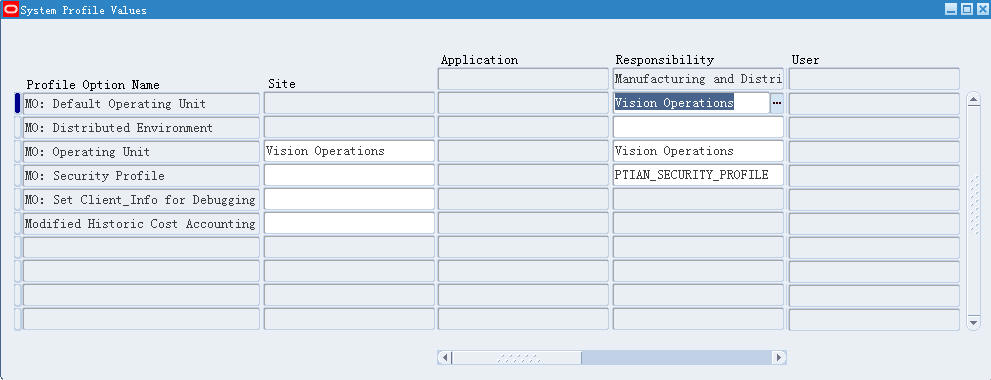
System Admin职责下,Profile > System,设置MO: Security Profile为刚刚定义的'PTIAN_SECURITY_PROFILE'
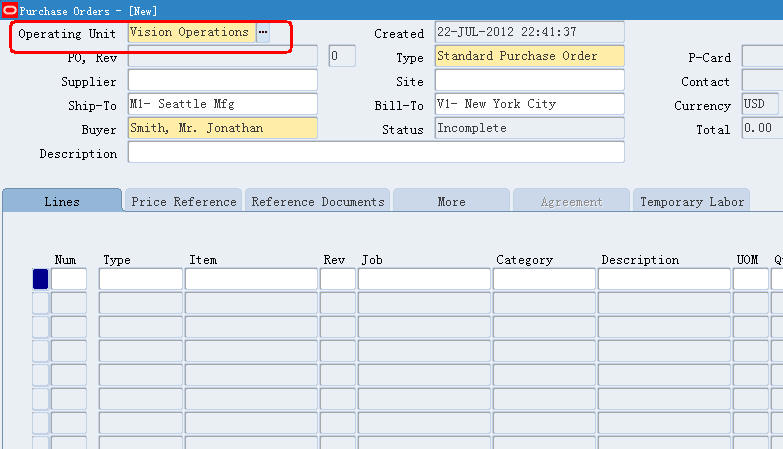
再切回Manufacturing and Distribution Manager职责,打开PO,这个时候,你就可以不切换职责的情况,定义三个OU下的采购订单了。
MOAC的实现原理-VPD技术
MOAC的实现是通过Oracle数据库的VPD(Virtual Private Database)技术来实现的。VPD技术提供了数据库对象(表,同义词,视图)行级别访问的控制。使用VPD技术可以有效地限制用户获取数据的范围。
Secooler 的一篇文章使用Oracle VPD(Virtual Private Database)限制用户获取数据的范围 讲VPD,里边的例子非常容易理解.
- --1.Create Data
- createtable t (x number);
- insertinto t values (1);
- insertinto t values (2);
- insertinto t values (10001);
- insertinto t values (10002);
- commit;
- select * from t;
- output:
- 1
- 2
- 10001
- 10002
- --2.Create VPD FUNCTION
- CREATEORREPLACEFUNCTION f_limited_query_t (s_schema IN VARCHAR2,
- s_object IN VARCHAR2)
- RETURN VARCHAR2
- AS
- BEGIN
- RETURN'X <= 10000';
- END;
- --3.Register VPD Policy.
- BEGIN
- DBMS_RLS.add_policy (object_schema => 'APPS',
- object_name => 'T',
- policy_name => 'POLICY_LIMITED_QUERY_T',
- function_schema => 'APPS',
- policy_function => 'F_LIMITED_QUERY_T');
- END;
- select * from t;
- output:
- 1
- 2
对于上边例子,我们对表T使用了VPD技术,引入了表限制Function f_limited_query_t,这样我们通过function限制了对表的查询,查询结果只返回小于10000的数字。
如何查看我们是否对某张表使用了VPD技术
SELECT * FROM DBA_POLICIES WHERE object_name = 'T';
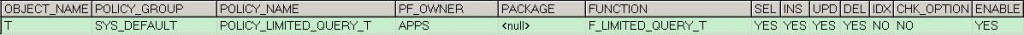
查询结果中,其中Pakcage + Function就是我们对于表所加的限制。
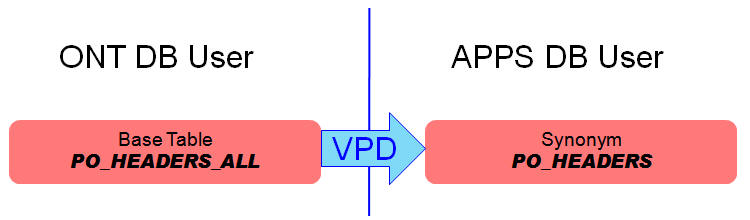
那么Oracle EBS是如何使用VPD技术来实现多组织的
R12里,以PO表为例,PO_HEADERS_ALL是基础表(PO/APPS Scehma),PO_HEADERS是PO_HEADERS_ALL对应的Synonym对象(Apps Schema),我们对PO_HEADERS应用VPD技术.MO_GLOBAL-Dive into R12 Multi Org Design有较为详细的说明,
In pre Release 12, you would have had following methodology for PO_HEADERS_ALLa. A table is created in PO Schema, named PO_HEADERS_ALLb. A synonym named PO_HEADERS_ALL is created in APPS schema, referring to PO.PO_HEADERS_ALLc. Create a view PO_HEADERS in APPS schema, as "select * from po_headers_all where org_id=client_info"But now in R12, following will happena. A table is created in PO Schema, named PO_HEADERS_ALLb. A synonym named PO_HEADERS_ALL is created in APPS schema, referring to PO.PO_HEADERS_ALLc. Another synonym named PO_HEADERS is created in APPS, referring to PO_HEADERS_ALLd. A Row Level security is applied to PO_HEADERS, using package function MO_GLOBAL.ORG_SECURITY.This can be double-checked by running SQL select * from all_policies where object_name='PO_HEADERS'e. The effect of this policy is that,whenever you access PO_HEADERS, Oracle RLS will dynamically append WHERE CLAUSE similar to belowSELECT * FROM PO_HEADERS WHERE EXISTS (SELECT 1 FROM mo_glob_org_access_tmp oa WHERE oa.organization_id = org_id)
看下下边Query的输出
SELECT * FROM DBA_POLICIES WHERE object_name = 'PO_HEADERS';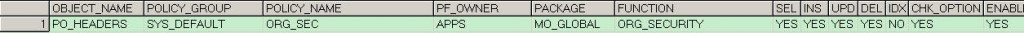
可以看到,我们对表PO_HEADERS加了MO_GLOBAL.ORG_SECURITY限制,MO_GLOBAL.ORG_SECURITY的作用实际上就是根据你关于MOAC Profiles的设置,然后转换为相应Where条件(组织过滤),再进行查询。
对于VPD表的查询
对于VPD表,简单的查询一般是不返回记录的,如果想查到记录,需要设置一下上下文先
--普通查询VPD表
select * from PO_HEADERS;--No Output
--Single OU Mode
BEGIN execute mo_global.set_policy_context('S',204); --204为ORG_ID,S表示Single Org ContextEND;select * from PO_HEADERS;--会输出OU:204下边的所有PO
--Multiple OU Mode(simulate login to a specific responsibility)
a. Call fnd_global.apps_initialize(userid,resp_id,resp_appl_id);
b. call MO_GLOBAL.INIT(p_appl_short_name);This will read the MO profile option values for your responsibility/user, and will initialize the Multi Org Access.
c.select * from po_headers
MOAC API
What is the purpose of MO_GLOBAL.ORG_SECURITY?
The purpose of Row-Level-Security is to hide certain data[based on some conditions]. RLS does so by appending a where clause to the secured object.1. MO_GLOBAL.ORG_SECURITY is a function that returns a predicate for the WHERE CLAUSE2. The where clause will be appended to Table/Synonym/View for which Multi Org Row Level security is enabled
What is the purpose of MO_GLOBAL.SET_POLICY_CONTEXT ?
This procedure has two parameters p_access_mode Pass a value "S" in case you want your current session to work against Single ORG_ID Pass a value of "M" in case you want your current session to work against multiple ORG_ID's p_org_id Only applicable if p_access_mode is passed value of "S"
MOAC相关的查询语句
Security Profile Definiation
- SELECT *
- FROM per_security_profiles
- WHERE security_profile_name = 'PTIAN_SECURITY_PROFILE';
check Organization which are related to a profile
- select PPO.*
- from PER_SECURITY_PROFILES PPR,
- PER_SECURITY_ORGANIZATIONS PPO
- where PPR.security_profile_id = PPO.security_profile_id
- and security_profile_name like'%PTIAN_SECURITY_PROFILE%';
- set long 10000
- set pagesize 500
- set linesize 160
- column SHORT_NAME format a30
- columnNAME format a40
- column LEVEL_SET format a15
- column CONTEXT format a30
- column VALUE format a40
- select p.profile_option_name SHORT_NAME,
- n.user_profile_option_name NAME,
- decode(v.level_id,
- 10001, 'Site',
- 10002, 'Application',
- 10003, 'Responsibility',
- 10004, 'User',
- 10005, 'Server',
- 10006, 'Org',
- 10007, decode(to_char(v.level_value2), '-1', 'Responsibility',
- decode(to_char(v.level_value), '-1', 'Server',
- 'Server+Resp')),
- 'UnDef') LEVEL_SET,
- decode(to_char(v.level_id),
- '10001', '',
- '10002', app.application_short_name,
- '10003', rsp.responsibility_key,
- '10004', usr.user_name,
- '10005', svr.node_name,
- '10006', org.name,
- '10007', decode(to_char(v.level_value2), '-1', rsp.responsibility_key,
- decode(to_char(v.level_value), '-1',
- (select node_name from fnd_nodes
- where node_id = v.level_value2),
- (select node_name from fnd_nodes
- where node_id = v.level_value2)||'-'||rsp.responsibility_key)),
- 'UnDef') "CONTEXT",
- v.profile_option_value VALUE
- from fnd_profile_options p,
- fnd_profile_option_values v,
- fnd_profile_options_tl n,
- fnd_user usr,
- fnd_application app,
- fnd_responsibility rsp,
- fnd_nodes svr,
- hr_operating_units org
- where p.profile_option_id = v.profile_option_id (+)
- and p.profile_option_name = n.profile_option_name
- andupper(p.profile_option_name) in ( select profile_option_name
- from fnd_profile_options_tl
- whereupper(user_profile_option_name)
- likeupper('%MO: Security Profile%'))
- and usr.user_id (+) = v.level_value
- and rsp.application_id (+) = v.level_value_application_id
- and rsp.responsibility_id (+) = v.level_value
- and app.application_id (+) = v.level_value
- and svr.node_id (+) = v.level_value
- and org.organization_id (+) = v.level_value
- orderBY short_name, user_profile_option_name, level_id, level_set;
支持MOAC功能的Form开发步骤
这部分摘自:http://bbs.erp100.com/thread-103395-1-1.html
在R12版本中,OU的控制采取了MOAC的方式,使用户的操作得到了改善。
而如果客户化的Form能够支持MOAC的功能,需要在界面上提供当前用户可以选择的OU字段供用户选择。
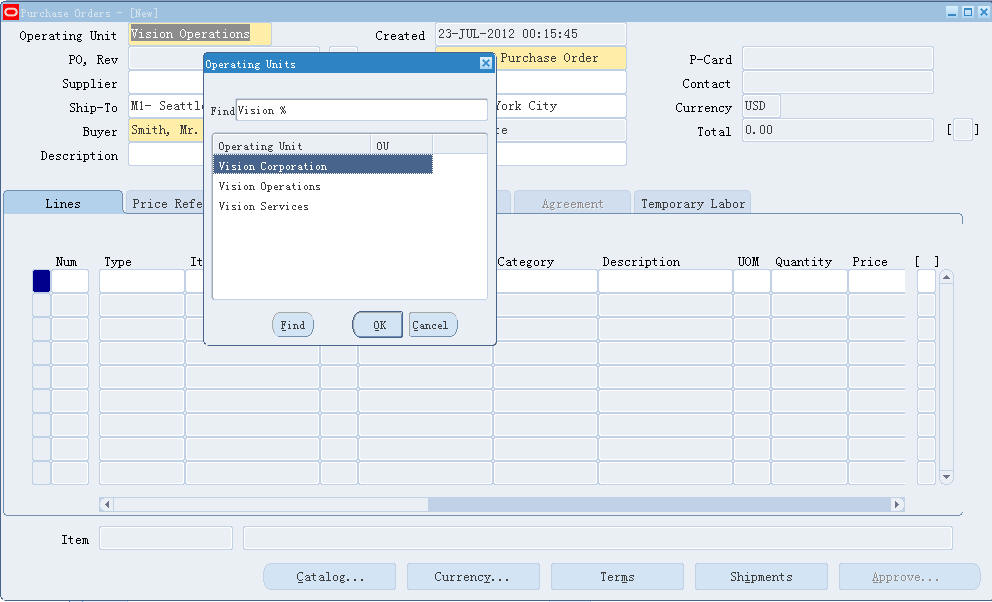
功能展示如下图:

这样在Form的开发过程中需要如下的开发步骤:
1,PRE-FORM 触发器初始化MOAC配置环境
添加如下代码:
MO_GLOBAL.init(‘ONT’);
— global.mo_ou_count
— global.mo_default_org_id
— global.mo_default_ou_name
IF l_default_org_id IS NOT NULL THEN — default org id not null
MO_GLOBAL.SET_POLICY_CONTEXT(‘S’,l_default_org_id);
ELSE
MO_GLOBAL.SET_POLICY_CONTEXT(‘M’,null);
END IF; — default org id not null
这段代码的作用是根据预制文件的设置,初始化OU的信息,将用户可以访问的OU信息插入到mo_glob_org_access_tmp表中,
同时将默认的OU ID、OU Name和OU Count分别写到global.mo_default_org_id, global.mo_default_org_id, global.mo_default_ou_name
具体细节可以查看数据库包:mo_global
2,WHEN-CREATE-RECORD触发器中拷贝OU默认值
在此触发器中将默认的OU ID和OU Name拷贝给Form界面上对应的自动,实现创建记录的时候默认带出默认OU信息。
copy(name_in(‘global.mo_default_org_id’),’’);
copy(name_in(‘global.mo_default_ou_name’),’’);
3,创建OU的LOV
Form界面上的OU 名称字段创建一个LOV,LOV对应记录组的SQL语句如下:
SELECT hr.organization_id organization_id, hr.NAME organization_name
FROM hr_operating_units hr
WHERE mo_global.check_access(hr.organization_id) = ‘Y’
ORDER BY organization_name
其它没有特殊的步骤。
MindMap
参考:
Oracle Applications Multiple Organizations Implementation Guide
EBS R12 MOAC(Multi-Org Access Control)原理探索
MO_GLOBAL-Dive into R12 Multi Org Design
FAQ - Multiple Organizations Architechure (Multi-Org) (Doc ID 165042.1)
Note 745420.1 -How To Setup And Check MO / MOAC Setup In APPS Instance At R12 Level - Precedence of MO - MOAC Profile Options
Best Practices for Securing the E-Business Suite [ID 189367.1]
Best Practices For Securing Oracle E-Business Suite Release 12 [ID 403537.1]
Understanding and Using HRMS Security in Oracle HRMS [ID 394083.1]
Security List Maintenance for All Profiles Is Excluding Employees [ID 755410.1]
Effect Of Security List Maintenance Concurrent Request within the Oracle HRMS Module [ID 457629.1]
转载请注明出处:http://blog.csdn.net/pan_tian/article/details/7774715
===EOF===